New & Notable
Get Started
How to deploy Intune compliance policies for iOS and iPadOS
Compliance policies are a significant part of IT's device management, so admins should learn about Intune's compliance management features for all types of devices.
Evaluate
3 best enterprise mobile app authentication methods
Mobile app authentication is a foundational security strategy for remote and hybrid workforces. Learn how to choose between passwords, multifactor authentication and biometrics.
Manage
How to create a mobile device security policy, with template
A well-defined mobile device security policy should educate employees on the proper use of BYODs and set clear standards for end users and IT administrators alike.
Problem Solve
8 mobile app development challenges for the enterprise
Despite the growth of mobile application development in the enterprise, developers must still navigate unique challenges to deliver apps to mobile users.
Trending Topics
-
Mobile Application Strategy Evaluate
3 best enterprise mobile app authentication methods
Mobile app authentication is a foundational security strategy for remote and hybrid workforces. Learn how to choose between passwords, multifactor authentication and biometrics.
-
Operating Systems & Devices Get Started
What is the Rabbit R1, and what can it offer the enterprise?
Is an AI-powered device the next step in AI development, or a marketing gimmick? IT must explore whether the Rabbit R1 and its operating system offer real business benefits.
-
Mobile Security Manage
How to create a mobile device security policy, with template
A well-defined mobile device security policy should educate employees on the proper use of BYODs and set clear standards for end users and IT administrators alike.
-
Mobile Infrastructure Evaluate
Could the iPhone 15's USB-C port drive device consolidation?
With the coming of the new iPhone with the USB-C port, organizations might look at this new compatibility feature as the impetus for some changes to their device policies.
-
Mobile Management Get Started
How to deploy Intune compliance policies for iOS and iPadOS
Compliance policies are a significant part of IT's device management, so admins should learn about Intune's compliance management features for all types of devices.
-
Unified endpoint management Get Started
Creating a patch management policy: Step-by-step guide
A comprehensive patch management policy is insurance against security vulnerabilities and bugs in networked hardware and software that can disrupt your critical business processes.
Find Solutions For Your Project
-
Evaluate
3 best enterprise mobile app authentication methods
Mobile app authentication is a foundational security strategy for remote and hybrid workforces. Learn how to choose between passwords, multifactor authentication and biometrics.
-
4 types of mobile security models and how they work
-
The ultimate guide to mobile device security in the workplace
-
BYOD's outlook brightens in hybrid workplaces
-
-
Problem Solve
8 mobile app development challenges for the enterprise
Despite the growth of mobile application development in the enterprise, developers must still navigate unique challenges to deliver apps to mobile users.
-
How to set up Apple Pay for a business
-
How do personal hotspots work for remote work?
-
Does a hotspot work when a mobile device has no service?
-
-
Manage
How to create a mobile device security policy, with template
A well-defined mobile device security policy should educate employees on the proper use of BYODs and set clear standards for end users and IT administrators alike.
-
Top 4 mobile security threats and challenges for businesses
-
What fees come with accepting Apple Pay for businesses?
-
Improve mobile hotspot security in 5 steps
-
Mobile Computing Basics
-
Get Started
What is the Rabbit R1, and what can it offer the enterprise?
Is an AI-powered device the next step in AI development, or a marketing gimmick? IT must explore whether the Rabbit R1 and its operating system offer real business benefits.
-
Get Started
How to deploy Intune compliance policies for iOS and iPadOS
Compliance policies are a significant part of IT's device management, so admins should learn about Intune's compliance management features for all types of devices.
-
Get Started
4G (fourth-generation wireless)
4G is the short name for fourth-generation wireless, the stage of broadband mobile communications that supersedes 3G (third-generation wireless) and is the predecessor of 5G (fifth-generation wireless).
Multimedia
-
News
View All -
Mobile operating systems and devices
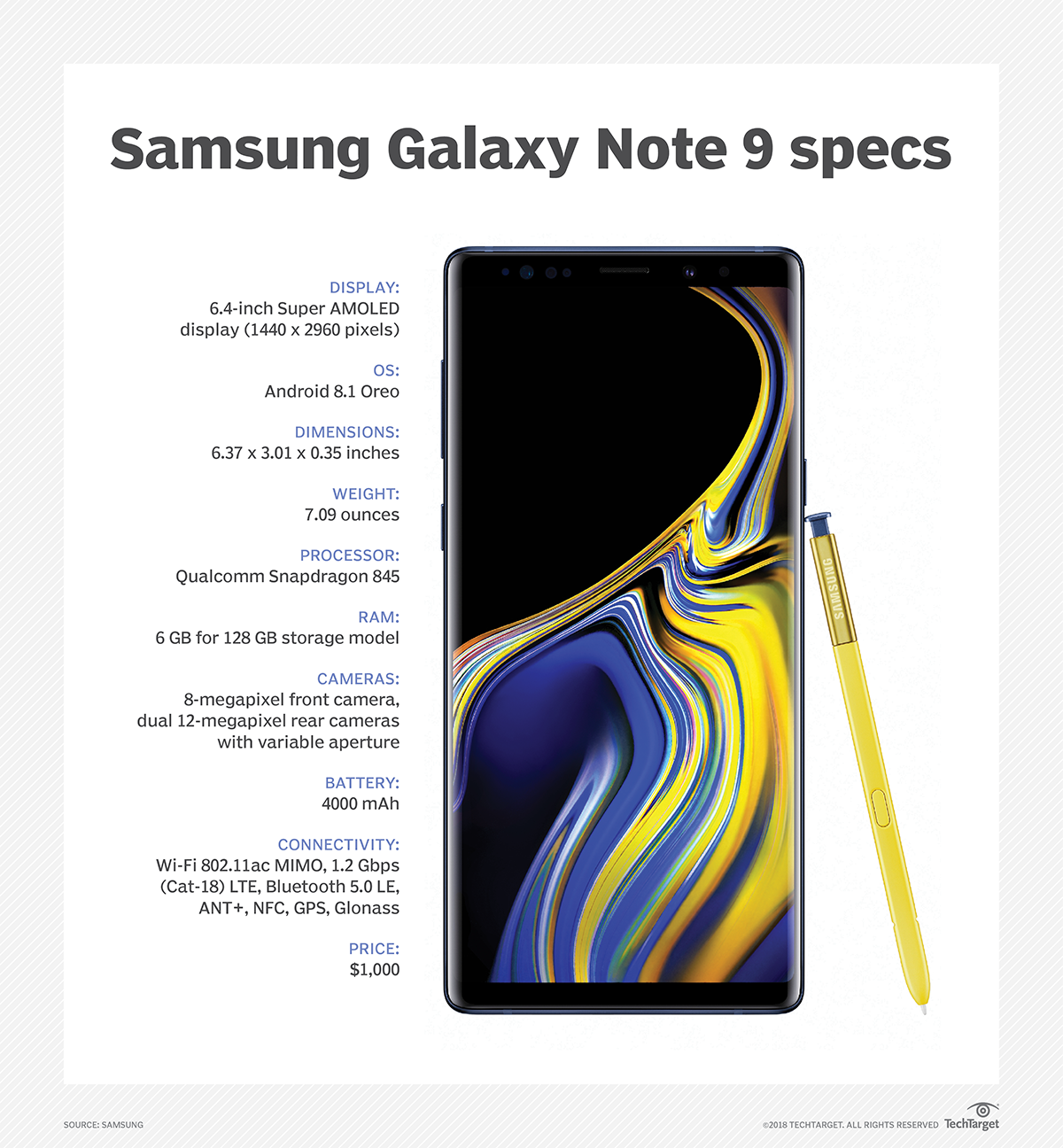
Samsung seeks bigger role as a business mobile provider
Samsung's wide variety of mobile devices, partnerships with software makers and government-grade security are differentiators in the business market, analysts said.
-
Mobile management
Jamf Q&A: How simplified BYOD enrollment helps IT and users
Jamf executives at JNUC 2022 share their vision of the future with simplified BYOD enrollment and the role iPhones have in the enterprise.
-
Mobile security
Jamf to acquire ZecOps to bolster iOS security
Jamf will pay an undisclosed sum for ZecOps, which logs activity on iOS devices to find potential attacks. The companies expect the deal to close by 2023.